In the intricate tapestry of the digital age, a particular group plays a pivotal role in the collection and dissemination of personal details. These entities, often operating in the shadows of the internet, are instrumental in shaping the contours of our digital footprints. This section delves into the mechanisms and implications of their operations, shedding light on the complex dynamics of information exchange in the modern world.
Understanding the Role of Information Intermediaries
Information intermediaries are entities that specialize in gathering and selling personal data. This practice, while often opaque to the average user, is a cornerstone of many digital services and marketing strategies. These facilitators compile vast databases, which are then utilized by various organizations to tailor their services or products to specific demographics.
The Impact on Personal Autonomy
The activities of these intermediaries have profound implications for individual autonomy and choice. By aggregating and analyzing personal information, they influence the flow of targeted advertisements and the customization of online experiences. This raises significant concerns regarding the balance between convenience and privacy, as users often unknowingly trade their personal details for access to various online platforms and services.
As we navigate through the digital landscape, it becomes crucial to understand the mechanisms through which our information is collected, used, and potentially misused. This awareness is the first step towards safeguarding our digital identities and ensuring that our interactions online are both beneficial and respectful of our autonomy.
Understanding Data Brokers
This section delves into the pivotal roles and definitions of entities that manage your online privacy vast amounts of personal information. These entities operate within a complex framework, influencing various aspects of modern digital life.
Data brokers, often referred to as information resellers, are companies that collect, analyze, and sell or provide access to large databases of personal information. This information is typically used for a variety of purposes, including marketing, risk mitigation, and enhancing user experiences across digital platforms.
- Collection of Information: These entities gather data from numerous sources, including public records, social media, and online transactions.
- Analysis and Segmentation: After collection, the data is analyzed and segmented based on various criteria such as demographics, purchasing behavior, and lifestyle choices.
- Distribution of Data: The processed information is then made available to other businesses, government agencies, or research institutions, often tailored to specific needs or objectives.
The role of data brokers is multifaceted, encompassing both the facilitation of targeted advertising and the provision of critical data for risk assessment and fraud prevention. However, their activities also raise significant concerns regarding the privacy and security of personal information.
Regulatory oversight varies by region, with some jurisdictions implementing strict guidelines to protect consumer data, while others have more lenient frameworks. Understanding the regulatory environment is crucial for both data brokers and consumers to navigate the implications of data sharing effectively.
In conclusion, data brokers play a significant role in the digital economy, influencing how personal information is used and distributed. Their activities require careful scrutiny to balance the benefits of data utilization with the protection of individual privacy rights.
Definition and Role of Data Brokers
This section delves into the historical context and developmental trajectory of the information intermediary sector. Understanding the roots and evolution of this industry provides crucial insights into its current operations and potential future directions.
The inception of information intermediaries can be traced back to the early days of digital data accumulation. Initially, these entities primarily focused on collecting and selling basic demographic details. Over time, as technology advanced and the internet became ubiquitous, their scope and methodologies expanded significantly.
- **Early Beginnings**: In the late 20th century, these firms started as simple aggregators of public records and basic consumer information.
- **Technological Advancements**: The advent of the internet and sophisticated data analytics tools allowed these entities to collect and analyze vast amounts of data, enhancing their capabilities and offerings.
- **Expansion of Data Sources**: As the digital footprint of individuals grew, so did the sources from which these firms could gather information, including social media, online shopping, and various digital platforms.
- **Shift in Business Models**: Initially selling simple lists of names and contact details, these firms evolved to offer complex data analytics services, predictive modeling, and targeted marketing solutions.
The evolution of this sector reflects a broader societal shift towards data-driven decision-making across various industries. This transformation has not only expanded the operational scope of these entities but also raised significant ethical and privacy concerns, which are critical to address in contemporary discussions about data governance and consumer rights.
In summary, the developmental journey of information intermediaries from simple data aggregators to sophisticated data analytics firms underscores the integral role they play in modern data-driven economies. Their evolution is a testament to the dynamic interplay between technological innovation and evolving business needs.
Origins and Evolution of the Data Broker Industry
This section delves into the historical background and the progression of the information intermediary sector. It explores how these entities have transformed over time, adapting to technological advancements and regulatory changes, ultimately shaping the landscape of personal data management and exchange.
Initially, these entities primarily focused on gathering basic demographic details such as names, addresses, and phone numbers. However, as technology evolved, so did their capabilities and the scope of information they could amass. Today, the types of data collected by these intermediaries are vast and varied, encompassing a wide range of personal and behavioral details.
- **Demographic Data**: This includes basic personal information like age, gender, marital status, and education level.
- **Financial Data**: Details about an individual’s financial status, including credit scores, banking information, and investment patterns.
- **Behavioral Data**: Insights into consumer habits and preferences, derived from online activities, shopping patterns, and social media interactions.
- **Location Data**: Information about an individual’s whereabouts, often collected through mobile devices and GPS technologies.
- **Health Data**: Sensitive information related to an individual’s health status, medical history, and insurance details.
- **Online Activity Data**: Data collected from internet browsing, including search history, website visits, and online purchases.
The evolution of data collection methods has been significant, moving from traditional survey methods to sophisticated digital tracking and data mining techniques. This has expanded the depth and breadth of information available to these intermediaries, enhancing their ability to profile individuals and predict consumer behavior.
Understanding the types of data these entities collect is crucial for comprehending their impact on personal privacy and the strategies necessary for data protection. As the industry continues to evolve, it is essential to stay informed about these practices and advocate for stronger privacy protections.
Methods of Data Acquisition
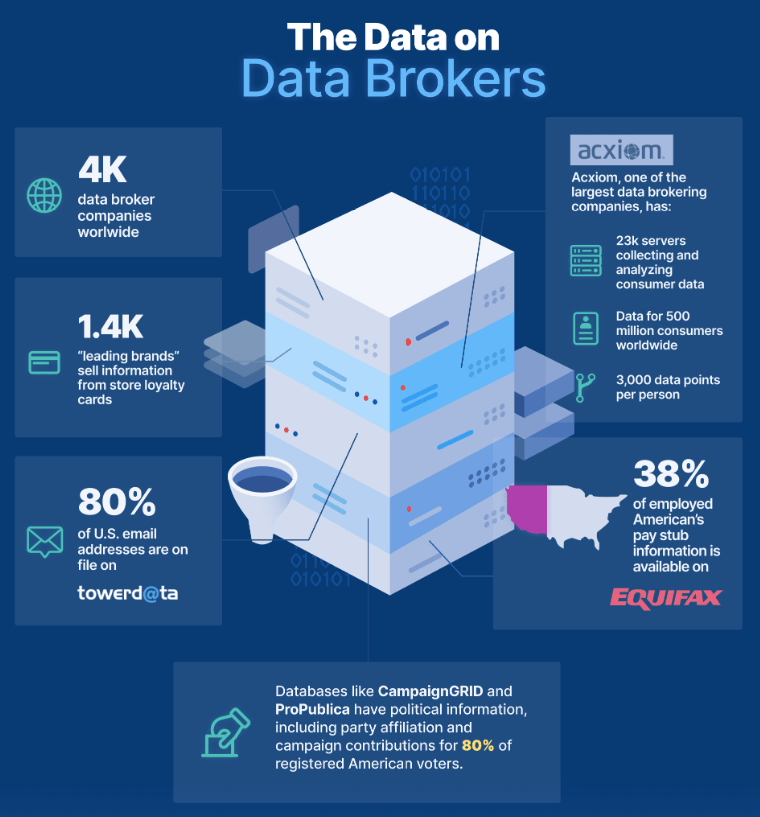
This section delves into the various tactics employed by entities in the information trade to gather personal details. Understanding these techniques is crucial for recognizing the breadth of surveillance and data collection in today’s digital landscape.
Web Tracking and Cookies: One common method involves the use of cookies and other tracking technologies embedded in websites. These tools monitor user activity across the internet, capturing browsing habits, search queries, and even the content of some interactions. This data is then aggregated and used to build comprehensive profiles of individuals.
Social Media Monitoring: Social platforms are a rich source of personal information. Entities in the data trade often tap into public profiles, posts, and interactions to extract details such as interests, relationships, and personal views. This data is particularly valuable due to its personal nature and the frequency of updates.
Purchase and Transaction Records: Another significant source of data is the records of purchases and financial transactions. This includes both online and offline transactions, providing insights into consumer behavior, spending patterns, and product preferences.
Public Records and Data Mining: Brokers also access public records, including property records, court documents, and other government-held information. Data mining techniques are applied to these records to extract and compile relevant personal details.
Subscription and Survey Data: Often, individuals provide personal information through subscriptions, surveys, and feedback forms. This data, willingly shared, is then collected and used by data aggregators to enhance their databases.
Each of these methods contributes to the vast pools of personal data that are traded and used in various industries. It is essential for consumers to be aware of these practices to better protect their personal information in the digital age.
Methods of Data Acquisition
This section delves into the intricate processes employed by entities to gather information. Understanding these mechanisms is crucial for comprehending the broader implications of information collection practices on individual privacy and digital rights.
Typically, these entities obtain data through various means, including but not limited to public records, online activities, and commercial transactions. Public records, such as property documents or court filings, are a primary source. These records are often accessible to the public and can be legally collected and analyzed.
Online activities represent another significant avenue for data collection. Every time an individual interacts with digital platforms, whether it be through social media, online shopping, or web browsing, they leave behind a trail of data. This data can include anything from search history to purchase patterns and is often collected through cookies or other tracking technologies.
Commercial transactions also play a crucial role in data acquisition. Whenever a purchase is made, whether online or in-store, the transaction details can be recorded and used. This includes not only what was purchased but also where and when, providing a wealth of information about consumer behavior and preferences.
Furthermore, these entities sometimes engage in data partnerships with other organizations. This collaborative approach allows them to expand their data pool significantly, often integrating data from disparate sources to create comprehensive profiles.
Each of these methods raises important questions about consent, privacy, and the ethical use of information. As such, it is essential for consumers and policymakers alike to understand these practices in order to safeguard personal information and ensure fair data practices.
How Data Brokers Use Collected Information
This section delves into the multifaceted ways in which information aggregators utilize the vast datasets they compile. Understanding these practices is crucial for grasping the broader implications of data collection on individual privacy and market dynamics.
Information aggregators employ a variety of strategies to leverage the data they gather. Here are some key methods:
- Targeted Advertising: One of the primary uses of collected data is to tailor advertisements to specific demographics or even individuals. By analyzing consumer behavior and preferences, these entities can help businesses deliver highly targeted marketing campaigns.
- Risk Assessment: Financial institutions often rely on data provided by these aggregators to assess creditworthiness and identify potential risks. This information can influence decisions on loans, insurance premiums, and even employment opportunities.
- Market Research: Companies use insights derived from aggregated data to understand market trends, consumer behavior, and potential gaps in the market. This helps in developing new products or refining existing ones.
- Fraud Detection: Data from various sources can be cross-referenced to detect and prevent fraudulent activities. This is particularly important in sectors such as finance and e-commerce.
- Personalization: Services and products are increasingly personalized based on the data collected. This ranges from personalized shopping experiences to tailored content on digital platforms.
The impact of these practices on consumer privacy is significant. As information aggregators continue to expand their capabilities, the line between public and private information becomes increasingly blurred. This raises important questions about consent, transparency, and the ethical use of personal data.
Regulatory frameworks are beginning to address these concerns, but the evolving nature of data collection and usage requires ongoing vigilance and adaptation. Consumers must also play an active role in protecting their data by understanding their rights and the tools available to safeguard their information.
In conclusion, the utilization of collected data by information aggregators is a complex and evolving field with profound implications for privacy, market dynamics, and consumer rights. As technology advances, so too must our strategies for managing and regulating these practices.
Impact on Consumer Privacy
This section delves into the profound effects that information intermediaries have on individual privacy. As these entities gather and utilize personal details, the implications for privacy are extensive and multifaceted.
Information intermediaries operate within a complex regulatory landscape that varies by region and jurisdiction. Here are some key regulatory frameworks that govern their activities:
- General Data Protection Regulation (GDPR) – Enacted by the European Union, this regulation imposes strict rules on the collection, processing, and transfer of personal data. It grants individuals significant rights over their data, including the right to access, rectify, and erase their information.
- California Consumer Privacy Act (CCPA) – This U.S. legislation provides California residents with the right to know what personal information is being collected about them, the right to say no to the sale of their information, and the right to equal service and price, even if they exercise their privacy rights.
- Federal Trade Commission (FTC) Regulations – In the United States, the FTC plays a crucial role in overseeing the activities of information intermediaries, ensuring they adhere to consumer protection laws and addressing deceptive practices.
- Personal Data Protection Act (PDPA) in Singapore – This act governs the collection, use, and disclosure of personal data by commercial entities, emphasizing consent, accountability, and the rights of individuals regarding their data.
These regulations aim to balance the economic interests of information intermediaries with the fundamental rights of individuals to privacy and data protection. Compliance with these frameworks is essential for these intermediaries to operate legally and ethically.
However, the enforcement of these regulations can be challenging due to the global nature of the internet and the digital economy. Cross-border data flows and varying interpretations of privacy laws complicate the regulatory environment. Consumers often find it difficult to navigate these complexities and protect their privacy effectively.
In conclusion, while regulatory frameworks provide a foundation for protecting consumer privacy, ongoing vigilance and adaptation are necessary to address the evolving challenges posed by information intermediaries in the digital age.
Regulatory Frameworks Governing Data Brokers

This section delves into the complex landscape of legal and regulatory measures that aim to oversee the activities of entities involved in the collection and distribution of personal information. Understanding these frameworks is crucial for ensuring transparency and accountability in the handling of sensitive data.
Globally, various jurisdictions have implemented different strategies to regulate these entities. Here, we explore some of the key regulatory approaches:
- Data Protection Laws: Many countries have enacted comprehensive data protection laws that mandate specific practices for collecting, storing, and using personal data. These laws often include requirements for obtaining consent from individuals before their data is processed.
- Sector-Specific Regulations: In addition to general data protection laws, some sectors have specific regulations that apply to the collection and use of data within their industry. For example, healthcare and financial services sectors often have stringent rules to protect sensitive customer information.
- Transparency Requirements: Regulations may require these entities to disclose their data collection practices, including what data is collected, how it is used, and who it is shared with. This transparency helps consumers make informed decisions about their data.
- Fines and Penalties: To enforce compliance, regulatory bodies can impose significant fines and penalties on entities that fail to adhere to the established rules. This financial deterrent is a key component of regulatory enforcement.
- Consumer Rights: Regulations often include provisions that empower consumers, allowing them to access, correct, or delete their personal data held by these entities. This right to control one’s own information is a cornerstone of modern data protection laws.
As the digital landscape continues to evolve, so too do the regulatory frameworks governing these entities. It is essential for policymakers, businesses, and consumers to stay informed about these developments to ensure the effective protection of personal information.
Consumer Awareness and Protection Measures
In this section, we delve into the proactive steps individuals can take to safeguard their personal information in the digital realm. Understanding the mechanisms by which sensitive details are collected and utilized is crucial for implementing effective defense strategies.
Education and Vigilance: The first line of defense is awareness. Consumers must be educated about the practices employed by entities that aggregate personal data. This includes recognizing the signs of data collection and understanding the implications of sharing information online.
Opting Out: Many organizations provide options for individuals to remove their information from databases. This process, often referred to as opting out, can significantly reduce the visibility of one’s personal details to external parties. It is essential to follow the specific procedures outlined by each entity to ensure effective removal.
Strong Passwords and Two-Factor Authentication: Enhancing the security of personal accounts through robust password management and enabling two-factor authentication adds an additional layer of protection. This mitigates the risk of unauthorized access to sensitive data.
Privacy Settings: Adjusting privacy settings on social media platforms and other online services can limit the amount of information shared publicly. This proactive measure helps in controlling the flow of personal data to potential collectors.
Regular Monitoring: Keeping a close eye on financial statements, credit reports, and online accounts can help detect any unauthorized use of personal information. Early detection is key to minimizing potential damage from data breaches.
Legal Frameworks: Understanding the legal protections available is also vital. Laws and regulations vary by region, and knowing one’s rights can empower consumers to take legal action if necessary.
By combining these strategies, individuals can significantly enhance their protection against the misuse of personal data, ensuring a safer and more private digital experience.
Strategies for Protecting Personal Data
In this section, we delve into effective methods individuals can employ to safeguard their sensitive information from unauthorized access and misuse. Understanding and implementing these strategies is crucial in maintaining control over one’s personal details in an increasingly interconnected world.
Below are several proactive measures that can significantly enhance data security:
- Strong Password Management: Utilize complex passwords and consider using a password manager to keep track of them securely. Regularly updating passwords can also deter unauthorized access.
- Two-Factor Authentication (2FA): Enable 2FA on all applicable accounts. This adds an extra layer of security by requiring a second form of verification, such as a text message or an authentication app, in addition to the password.
- Software Updates: Regularly update software and applications to patch security vulnerabilities. Many updates include fixes for known security issues that could be exploited by malicious actors.
- Secure Browsing Practices: Be cautious about the websites you visit and the links you click. Avoid suspicious sites and use secure connections (HTTPS) whenever possible.
- Data Encryption: Encrypt sensitive files and emails. Encryption transforms data into a format that can only be read with a decryption key, protecting it from being understood if intercepted.
- Limit Data Sharing: Be mindful of what personal information you share online and with whom. Only provide necessary details and review privacy settings on social media and other platforms regularly.
- Use of Virtual Private Networks (VPNs): VPNs can help protect your internet connection by encrypting your data and hiding your IP address, making it more difficult for others to track your online activities.
- Regular Data Audits: Periodically review what personal information is stored by various services and request deletion of unnecessary data. This helps minimize the amount of information available to potential threats.
By adopting these practices, individuals can significantly reduce the risk of their personal data being compromised, ensuring a safer digital experience.
Future Trends in Data Brokerage
In this section, we delve into the anticipated developments within the realm of information intermediation. As technology advances and societal norms evolve, it is crucial to understand how these changes might shape the practices of entities involved in the collection and distribution of personal data.
Emerging Technologies and Their Impact
Advancements in artificial intelligence and machine learning are set to revolutionize the way entities handle data. These technologies will enable more sophisticated analysis and prediction capabilities, potentially enhancing the value of data while also raising new ethical and privacy concerns.
Regulatory Evolution
With increasing public awareness and concern over privacy, regulatory frameworks are expected to become more stringent. This could lead to more transparent operations and stricter controls on the use of personal information, influencing how entities acquire and utilize data.
Consumer Empowerment
The trend towards empowering individuals with greater control over their personal information is likely to continue. Tools and services that facilitate data management and privacy protection will become more prevalent, allowing consumers to make informed decisions about their data.
Shift in Business Models
As awareness grows, there may be a shift from traditional data acquisition models to more consensual and transparent methods. Businesses might focus on building trust through ethical data practices, which could involve more explicit consent mechanisms and clearer communication about data usage.
Globalization and Data Flows
The global nature of data flows presents both opportunities and challenges. As data moves across borders, there will be a need for international cooperation and standards to ensure consistent protection and fair use of data. This could lead to new alliances and agreements between countries and regions.
Understanding these trends is essential for anyone involved in or affected by the activities of information intermediation. By staying informed, individuals and organizations can better prepare for the changes ahead and contribute to a more secure and respectful digital environment.